Last updated 12DEC2019
This is version 8 of my scripts to remove and block Windows 10 updates and related telemetry.
I’ve seen multiple posts at websites and forums telling folks how to deal with GWX. Most of them either don’t go far enough, or usually, they go way too far and break stuff.
This applies to Windows 7 ONLY.
Comments are closed after a while for security reasons. You can comment here if you like:
Remove And Block GWX In Windows 7 UPDATED 2
Since it has become obvious that this will be a running battle with Microsoft I’ve decided to make this page the permanent place to these scripts rather than a new post every time I update it.
You’ll need to check back here monthly for updates as Microsoft keeps re-releasing updates that in effect unhides them.
You’ll also want to keep the script handy and rerun it monthly for the same reason.
Thanks to:
Though info on all this stuff has come from dozens of sources, much of this info has come from the MDL forums.
In particular this thread: Remove Telemetry and Windows 10 Related Updates from Windows 7
Download my batch file: https://www.tweakhound.com/downloads/block_GWX_V8.zip
YOU MUST read the README.txt file.
The second half of this calls HideGWXetcV8.vbs to hide updates.
This will take a while.
DO NOT CLOSE WINDOW UNTIL YOU SEE: ” – Finished … All operations complete. Reboot now. Press any key to continue . . .”
Inspiration for this came from a variety of sources but started HERE.
The level of support you will receive is equal to the amount you paid for this 😉
This folder contains:
BlockGWXetcV8.bat – Removes and Hides GWX related updates like in step 2 above.
HideGWXetcV8.vbs – Automatically run by the above .bat files. This hides the updates the batch file uninstalled.
README.txt – Instructions
th_add_CMDandTO.reg – Adds open command windows here (standard and admin) ,and Take Ownership to right-click.
The .bat file and the .vbs files MUST be in the same folder!
(code is listed below)
To do this:
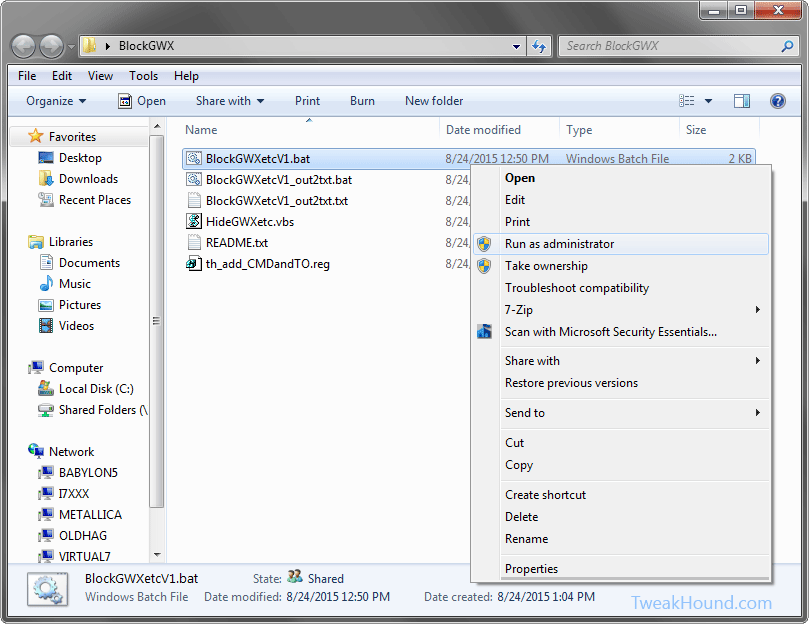
Either right-click the folder and choose Open Command Window Here as Administrator.
In the resulting command window type BlockGWXetcFINAL.bat and hit enter.
OR
right-click the BlockGWXetcFINAL.bat file (see above) and choose Run as Administrator.
If you do not have these right-click options, double-click in included th_add_CMDandTO.reg file and logout/reboot.
Let it run, when the .bat file runs HideGWXetc.vbs it will take a while.
It may look like things have stopped, they haven’t.
DO NOT CLOSE WINDOW UNTIL YOU SEE: ” – Finished … All operations complete. Reboot now. Press any key to continue . . .”
-END-

What how much more of this GWX in Win 7 cleanup crap do we have to endure?
I fear it will be a running battle through time.
Just got this a day or so ago in Windows Update:
KB3102812 (Windows 8) https://support.microsoft.com/en-us/kb/3102812
KB3102810 (Windows 7) https://support.microsoft.com/en-us/kb/3102810
Another Windows 10 nagware? Or am I just being pessimistic? 🙂
Well it does contain Wu.upgrade.ps.dll so my guess would be it does involve Win10.
In addition I checked DWS lite and it has been added to that.
I’ve hidden the update myself.
KB2952664 reinstalls itself at every boot, even when hidden and with the automatic updates disabled. Checked on two different win7 machines. What to do?
Haven’t seen or heard of that issue. Maybe try DWSlite? http://dws.wzor.net/
It’s discussed here: https://answers.microsoft.com/en-us/windows/forum/all/unable-to-uninstall-update-kb2952664/1c0e8b8a-c79b-4998-b6be-f8134cef4e82?auth=1
I don’t like third parties even if they’re open source, if the OS cannot be fixed without insane hacks I might as well forget it.
For now I’ve disabled the task scheduler – Microsoft – Windows – Application Experience – ProgramDataUpdater, which is the main spyware feature of that update (hoping THAT doesn’t re-activate as well 😉
I understand about the third party thing.
In case anyone’s interested, I managed removing it by doing this (from one of the suggestions in the link):
Elevated prompt:
Figure out the package names:
dism /online /get-packages | findstr KB2952664
Copy the shown package names into notepad and then remove one by one:
dism /online /remove-package /PackageName:Package_for_KB2952664~31bf3856ad364e35~amd64~~6.1.1.3
Outstanding!
Thank you for the information you posted above. It was very useful and was responsible for cleaningout the KB update files in Downloads. Thank you also for posting the program code. This is what I used because I could not get a good download from where I was located.
I came across this “critical update” from Microsoft, Vulnerability in Microsoft Font Driver Could Allow Remote Code Execution (3079904). On the page on which it appears they thoughtfully provided a workaround that didn’t actually work. I got an error message about me being the owner and the file could not be changed. Here is the link: https://support.microsoft.com/en-us/kb/3079904. The work around is for 64 bit system at this link:https://technet.microsoft.com/library/security/MS15-078 . Unfortunately the batch file provided doesn’t work as advertised. Basically what you are downloading it appears is a short program that changes the name of a file to prevent it from being used. I copied and pasted it below. It did not change the name of the file. Could that be because I am now the owner after running BlockGWXetcV3_FULL.bat? Eric, let me know if you want me to run the Microsoft file again and post the cmd window screen shot.
For 64-bit systems:
Enter the following commands at an administrative command prompt:
cd “%windir%\system32”
takeown.exe /f atmfd.dll
icacls.exe atmfd.dll /save atmfd.dll.acl
icacls.exe atmfd.dll /grant Administrators:(F)
rename atmfd.dll x-atmfd.dll
cd “%windir%\syswow64”
takeown.exe /f atmfd.dll
icacls.exe atmfd.dll /save atmfd.dll.acl
icacls.exe atmfd.dll /grant Administrators:(F)
rename atmfd.dll x-atmfd.dll
Restart the system.
To change the file name I changed the permissions for this one instance. It took a few tries to get the permission changed. Great website. I found your website from a link about MS Spyware in a New American article written by C. Mitchell Shaw.
Shoot me an email with a screenshot: https://www.tweakhound.com/about/contact/
Any idea if there are any newer ones to avoid
watch this thread: Remove Telemetry and Windows 10 Related Updates from Windows 7
Please note: If username has a space in it, this portion will fail and may cause unexpected consequences:
takeown /f %localappdata%\GWX /r /d y
icacls %localappdata%\GWX /grant administrators:F /t
rmdir /s /q %localappdata%\GWX\
timeout 5
Suggest replacing with:
if exist “%localappdata%\GWX” (
takeown /f “%localappdata%\GWX” /r /d y
icacls “%localappdata%\GWX” /grant administrators:F /t
rmdir /s /q “%localappdata%\GWX\”
timeout 5
)
the quotes will work with usernames containing spaces.
– Jonathan